As we navigate the complexities of the digital age, the traditional password system has shown its age and vulnerabilities. In this article we provide insights about passwords and their evolution into the emerging passkeys. We explain how they’re poised to revolutionize our online security and user experience.
The Problem with Passwords
For years, passwords have been the cornerstone of digital security. Yet, their effectiveness has been continuously undermined by human error and sophisticated cyber threats. From weak password creation to the dangers of phishing attacks, the cracks in the foundation are undeniable.
MFA: Bridging the Gap to a Passwordless World
To address the shortcomings of passwords Multi-Factor Authentication (MFA) has been introduced. MFA enhances security by requiring users to provide two or more verification factors to gain access to their accounts, combining something they know (like a password), something they have (like a smartphone), or something they are (like a fingerprint).
As we transition from traditional passwords to the more secure and convenient passkeys, Multi-Factor Authentication (MFA) serves as an intermediary step.
MFA significantly reduces the risk of unauthorized access. However it is still prone to various kinds of attacks. It depends on the MFA technique used, but usually MFA does not fully protect from phishing attacks or Man-in-the-Middle attacks. When using email verification codes or SMS-based authentication, there are also technology-specific threats.
To address this MFA has evolved over the years. Maybe you remember the list of pre-generated one-time codes you received from your bank in the 90ties and early 2000s? After that providers moved on to use proprietary hardware tokens and time-based one-time passwords (TOTP). Today proprietary authentication apps are quite popular. Another approach is to make the need of MFA dependent on some risk metrics. This is often called adaptive MFA.
Common to all of these technologies is a poor user experience. The login experience is interrupted by multiple login steps. In most cases people need to use multiple apps. Sharing authentication credentials across various devices is complicated and in some cases impossible. Recovering lost credentials is cumbersome.
As a result, MFA is poorly adopted and only used when people are forced to use it. Passkeys aim to change this and improve all these shortcomings of passwords and MFA.
Enter Passkeys: A Game Changer
Passkeys are a secure and easy-to-use method of authentication. These unique digital keys eliminate the need for traditional passwords, providing a more secure and user-friendly authentication method. Using cryptographic techniques, Passkeys ensure a more secure and smooth login process across various devices and platforms.
How Passkeys Work Technically
Passkeys work by using a secure, cryptographic protocol. When a user registers the device creates a unique pair of cryptographic keys: a private key that remains securely on the user’s device and a public key that is stored on the server. Authentication is performed by the device proving it has the private key without transmitting it, ensuring a secure login without passwords.
This is the same technology and standard that has been used by FIDO tokens (https://fidoalliance.org/) for several years already. FIDO tokens are available from several vendors. The best known are probably Yubikey and Google’s Titan Key. These kinds of hardware tokens were introduced to make the storage of credentials tamper-proof. In fact you can think of Passkeys as virtual FIDO tokens. But why would you virtualize a hardware token? The answer is: User experience.
Advantages of Passkeys
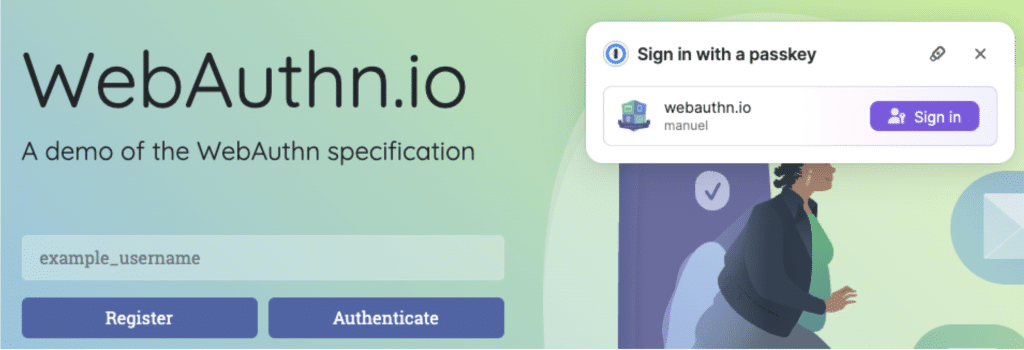
In addition to increased security, Passkeys also provide a superior user experience based on the WebAuthn standard. The login process with Passkeys is so smooth that you will hardly notice it. You can easily try it out at https://webauthn.io.
Registering a Passkey using 1Password. Just click “Save”.
Sign-in with Passkey using 1Password. Just click “Sign in”.
Passkeys are stored in and protected by the platform you use. This can be your Microsoft account, your Google account, your Apple account or whatever password manager you use. This means that to unlock your Passkeys, you simply use the authentication mechanism configured for your platform. This could be FaceID if you have an Apple device or Hello in case of a Microsoft platform.
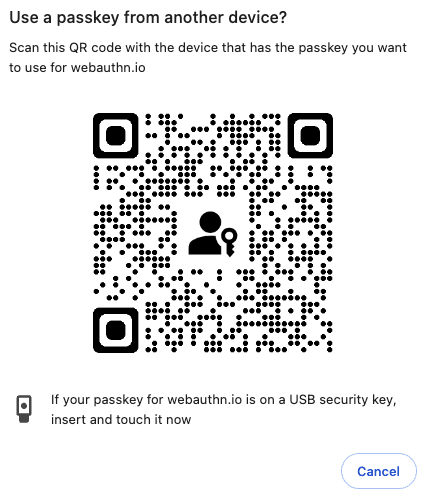
But what if I have an Android phone and I work on a Mac? This also works. You can use the credentials stored on your phone to sign in to a website on your desktop across platforms.
Use a passkey stored on another device by scanning a QR code.
Okay, great. But what if I lose my device? That problem is solved, too. Your Passkeys are attached to your user account and synchronized across all your devices via the cloud.
So to summarize the benefits:
- Increased Security: Passkeys are resistant to phishing, require no shared secrets, and significantly reduce the risk of account breaches.
- Seamless User Experience: They simplify the login process, making access to services faster and more convenient without compromising security.
- Cross-platform support. You can use Passkeys across multiple platforms.
Conclusion
Passkeys have the potential to revolutionize the way we authenticate on the Web. This is not only because of their superior security and user experience, but also because they are cross-platform and are easy to recover.
Nevertheless there are a few things to consider especially for high security applications.
- User onboarding: Passkeys do not solve the challenges of user onboarding. When registering a Passkey as credential for a Web site, you must identify the user. This challenge is not specific to passkeys, so a robust user onboarding process is required for all types of credentials.
- Dependence on platform security: As explained above the Passkeys are managed and protected by the platforms. Therefore you need to trust the platform provider to store and protect the Passkeys appropriately. While this level of security is more than sufficient for most applications, it may be a consideration for higher security requirements (e.g. e-banking applications).
- User acceptance: While Passkeys offer superior security and user experience, some users may find it much magic. They may question the security because it seems too easy to them (Hey, why am I logged in now? I didn’t even enter a password!)